ZAP (Zed Attack Proxy) is a widely used open-source web application security scanner. It’s free, Apache 2.0 licensed, and has no paid tiers or feature restrictions.
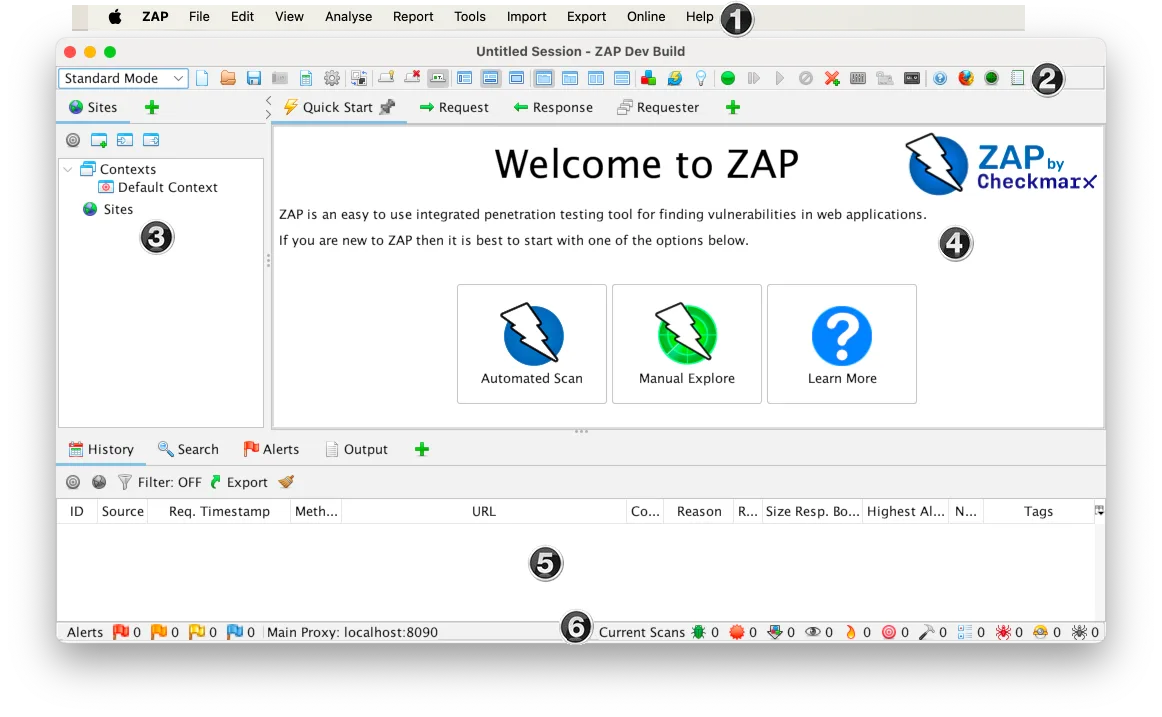
With 14,700+ GitHub stars, 2,500+ forks, and 229+ contributors, ZAP is a go-to free DAST tools choice for security teams, pentesters, and developers. Version 2.17.0 shipped in December 2025, written primarily in Java (73% of the codebase).
In September 2024, Checkmarx partnered with the ZAP project and hired all three project leaders — Simon Bennetts, Rick Mitchell, and Yiannis Pavlosoglou. ZAP remains free and open source. Checkmarx provides funding and resources for continued development.
What is ZAP?
ZAP sits between your browser and the target application as an intercepting proxy. All HTTP/HTTPS traffic passes through ZAP, where you can inspect, modify, and replay requests in real-time.
Beyond manual testing, ZAP includes automated scanning: a spider that crawls the application, an AJAX spider that uses a headless browser for JavaScript-heavy pages, a passive scanner that analyzes traffic without sending extra requests, and an active scanner that fires attack payloads at discovered endpoints.
The tool earned OWASP Flagship Project status and has been a GitHub Top 1000 project.
| Feature | Details |
|---|---|
| License | Apache 2.0 (free, no restrictions) |
| GitHub stars | 14,700+ |
| Contributors | 229+ |
| Language | Java (73%) |
| Latest version | 2.17.0 (December 2025) |
| API testing | REST, GraphQL, SOAP |
| Automation | YAML-based framework |
| Desktop platforms | Windows, macOS, Linux |
| Docker images | zap-stable, zap-weekly |
| CI/CD | Official GitHub Actions, GitLab templates |
| Output formats | HTML, JSON, XML, Markdown, SARIF |
| Maintained by | Checkmarx (all 3 project leaders employed) |
Key Features
Intercepting Proxy
ZAP’s core is the man-in-the-middle proxy. Configure your browser to route traffic through ZAP and you can:
- Inspect every request and response in real-time
- Modify parameters, headers, and request bodies before they reach the server
- Replay requests with altered values (fuzzing, parameter tampering)
- Record authentication sequences for automated replay
- Decrypt SSL/TLS traffic with ZAP’s installed CA certificate
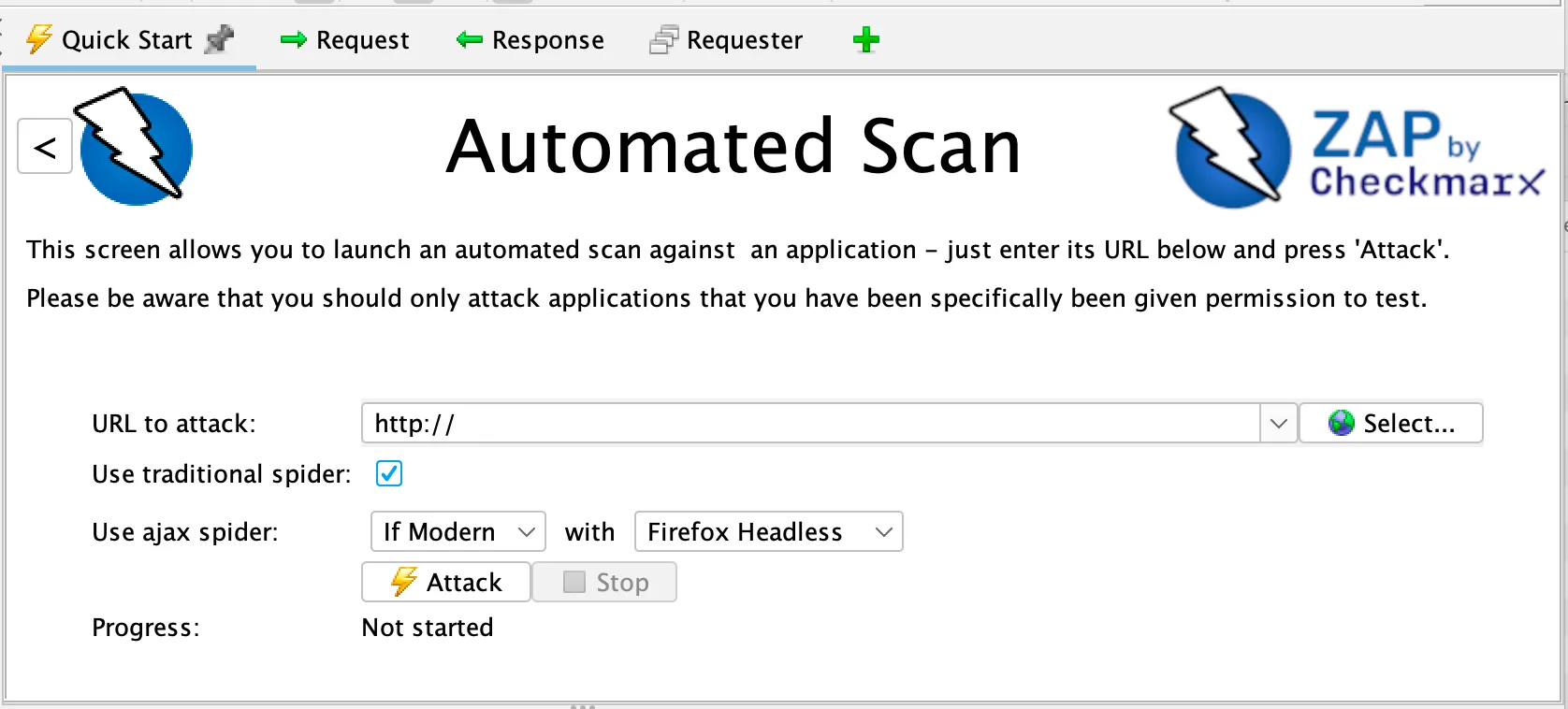
Spider and Active Scanner
ZAP combines two crawling approaches:
- Traditional Spider: Follows HTML links, submits forms, extracts URLs from JavaScript. Fast but misses dynamically generated content.
- AJAX Spider: Launches a headless browser (Firefox or Chrome) that executes JavaScript. Catches SPA routes, client-side navigation, and AJAX endpoints. Slower but more thorough for modern apps.
After crawling, the Active Scanner fires attack payloads against every discovered parameter and endpoint. The Passive Scanner runs continuously in the background, analyzing all proxied traffic for security issues without sending additional requests.
API Scanning
ZAP imports API definitions and tests each endpoint:
# Import and scan an OpenAPI spec
zap-api-scan.py -t https://example.com/openapi.json -f openapi
# GraphQL scanning
zap-api-scan.py -t https://example.com/graphql -f graphql
# SOAP WSDL scanning
zap-api-scan.py -t https://example.com/service.wsdl -f soap
Automation Framework
The YAML-based automation framework is how most teams integrate ZAP into CI/CD:
env:
contexts:
- name: "Default Context"
urls:
- "https://example.com"
authentication:
method: "form"
parameters:
loginUrl: "https://example.com/login"
loginRequestData: "username={%username%}&password={%password%}"
users:
- name: "testuser"
credentials:
username: "[email protected]"
password: "testpass123"
jobs:
- type: spider
parameters:
context: "Default Context"
user: "testuser"
maxDuration: 5
- type: spiderAjax
parameters:
context: "Default Context"
maxDuration: 5
- type: passiveScan-wait
parameters:
maxDuration: 10
- type: activeScan
parameters:
context: "Default Context"
user: "testuser"
- type: report
parameters:
template: "traditional-html"
reportFile: "zap-report.html"
Add-On Marketplace
ZAP’s marketplace has hundreds of extensions:
- Additional scan rules for specific technologies
- Import/export formats (HAR, OpenAPI, Postman)
- Reporting templates
- Authentication handlers
- Custom scripting (JavaScript, Python, Zest)
zap-baseline.py — it runs a passive-only scan that completes quickly without sending attack traffic. Use zap-full-scan.py for scheduled weekly or nightly scans that include active scanning. This keeps PR checks fast while still getting thorough coverage on a regular schedule.Installation
Desktop
Download from zaproxy.org/download/:
- Windows: MSI installer or portable ZIP
- macOS: DMG installer
- Linux: DEB, RPM, Snap (
sudo snap install zaproxy --classic), or TAR.GZ
Docker
# Stable image
docker pull zaproxy/zap-stable
# Baseline scan (passive only, fast)
docker run -t zaproxy/zap-stable zap-baseline.py \
-t https://example.com
# Full scan (active scanning)
docker run -t zaproxy/zap-stable zap-full-scan.py \
-t https://example.com -j
# API scan
docker run -t zaproxy/zap-stable zap-api-scan.py \
-t https://example.com/openapi.json -f openapi
# Daemon mode for API access
docker run -u zap -p 8080:8080 zaproxy/zap-stable \
zap.sh -daemon -host 0.0.0.0 -port 8080
Package Managers
# macOS
brew install --cask zap
# Linux (Snap)
sudo snap install zaproxy --classic
# Windows (Chocolatey)
choco install zap
Getting Started
Integrations
CI/CD Integration
GitHub Actions
name: ZAP Security Scan
on:
push:
branches: [main]
pull_request:
jobs:
zap-baseline:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Start application
run: docker-compose up -d && sleep 30
- name: ZAP Baseline Scan
uses: zaproxy/[email protected]
with:
target: 'http://localhost:8080'
rules_file_name: '.zap/rules.tsv'
cmd_options: '-a'
- uses: actions/upload-artifact@v4
if: always()
with:
name: zap-report
path: report_html.html
GitLab CI
zap-baseline:
stage: security
image: zaproxy/zap-stable
script:
- mkdir -p /zap/wrk
- zap-baseline.py -t $CI_ENVIRONMENT_URL
-g gen.conf -r zap-report.html
-J zap-report.json || true
artifacts:
paths:
- zap-report.html
reports:
dast: zap-report.json
ZAP vs Burp Suite
| Aspect | ZAP | Burp Suite Pro |
|---|---|---|
| Cost | Free | $499/year per user |
| License | Apache 2.0 | Proprietary |
| Detection accuracy | Good | Slightly better |
| CI/CD integration | Excellent (official Actions) | Good (Enterprise only) |
| Extensibility | Open marketplace | BApp Store |
| API scanning | REST, GraphQL, SOAP | REST, GraphQL, SOAP |
| Manual testing | Full proxy + tools | More polished UI |
| Community | Large open-source community | Strong commercial support |
When to Use ZAP
ZAP is the right choice when you want capable DAST scanning without licensing costs. The automated scanning, API testing, and CI/CD integration are genuinely good — not just “good for free software.”
Good fit for:
- Teams that need DAST without budget for commercial tools
- CI/CD pipelines needing automated security scanning with official GitHub Actions
- Security professionals learning pentesting techniques
- Open-source projects that want OSS-only tooling
- Manual penetration testing alongside automated scanning
- Organizations that want scan configuration as code (YAML automation framework)
Not the best fit if:
- You need vendor support SLAs and guaranteed response times
- You want managed scanning (enterprise tools like Invicti or Veracode DAST handle that)
- You need executive-level compliance dashboards out of the box
- Your team has no appetite for learning a tool with a steeper initial learning curve
History
ZAP started as a fork of Paros Proxy in 2010. Simon Bennetts, the original project lead, has said that by 2014 only about 20% of ZAP’s code came from Paros — the rest was built from scratch.
The project achieved OWASP Flagship status.
In September 2024, Checkmarx partnered with ZAP and hired all three project leaders. Checkmarx committed to keeping ZAP free and open source while providing resources for continued development.
Note: Now branded as ZAP by Checkmarx. In September 2024, Checkmarx joined forces with ZAP and employs all three project leaders. Still free, still open source under Apache v2 license.

Comments
Powered by Giscus — comments are stored in GitHub Discussions.