Tenable Web App Scanning is a cloud-based DAST solution built on the Nessus scanning engine. It tests web applications and APIs for security vulnerabilities and ties into Tenable’s Attack Surface Management for automatic discovery of web properties you might not know about.
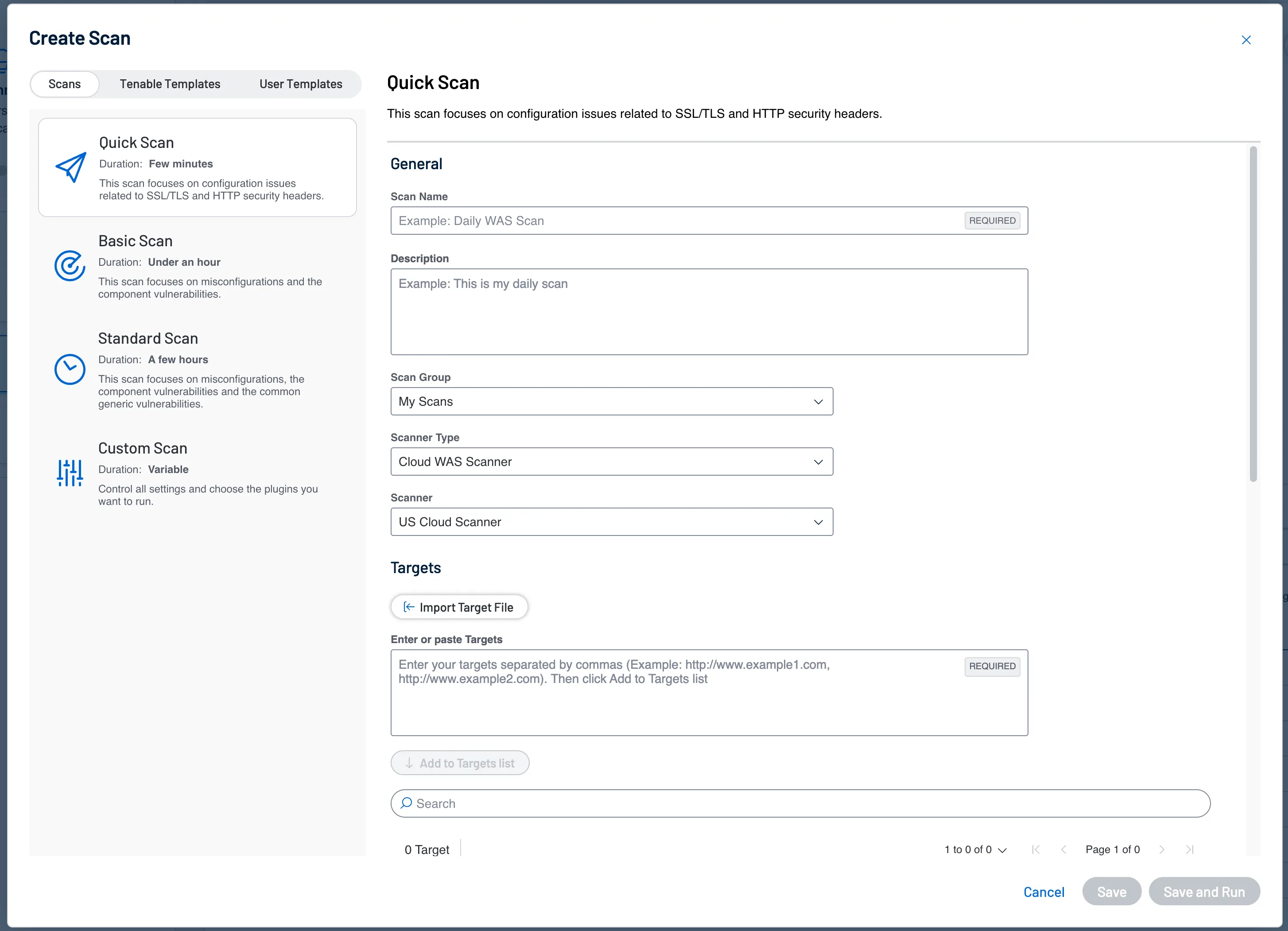
Pricing starts at $3,578 per year for 5 FQDNs. The scanner is also included in Tenable Vulnerability Management trials.
What is Tenable Web App Scanning?
Tenable WAS crawls running web applications through the front end, builds a site map of pages, links, and forms, then tests each one for vulnerabilities. It covers the OWASP Top 10, vulnerable third-party components, and API-specific flaws.
The Nessus engine underneath gets regular vulnerability check updates from Tenable’s research team. The cloud delivery means no infrastructure to manage — you point it at a URL and go.
Where Tenable WAS gets interesting is the Attack Surface Management integration. Tenable ASM continuously discovers web applications and APIs across your digital footprint, including shadow IT properties that security teams may not be tracking. When ASM finds an unknown web app, WAS can scan it automatically.
| Feature | Details |
|---|---|
| Engine | Nessus-powered scanning technology |
| Delivery | Cloud-native SaaS |
| On-premises option | Via Tenable Security Center (FedRAMP-authorized) |
| API testing | REST, GraphQL, SOAP |
| Pricing | From $3,578/year for 5 FQDNs |
| Rapid scans | Under 2 minutes for hygiene checks |
| SPA support | Modern JavaScript frameworks |
| Scan controls | Pause/resume, rate limiting, scheduling |
| ASM integration | Automatic web app discovery |
| Ecosystem | Tenable One, Tenable.io, Tenable.sc |
Key Features
API Security Testing
Tenable WAS tests three API types:
- REST APIs: Automated endpoint discovery and testing
- GraphQL: Query analysis and mutation testing
- SOAP Web Services: WSDL-based testing for legacy services
- OpenAPI Import: Feed in an OpenAPI/Swagger spec to guide API testing
- Authentication: OAuth 2.0, API keys, JWT, and custom auth methods
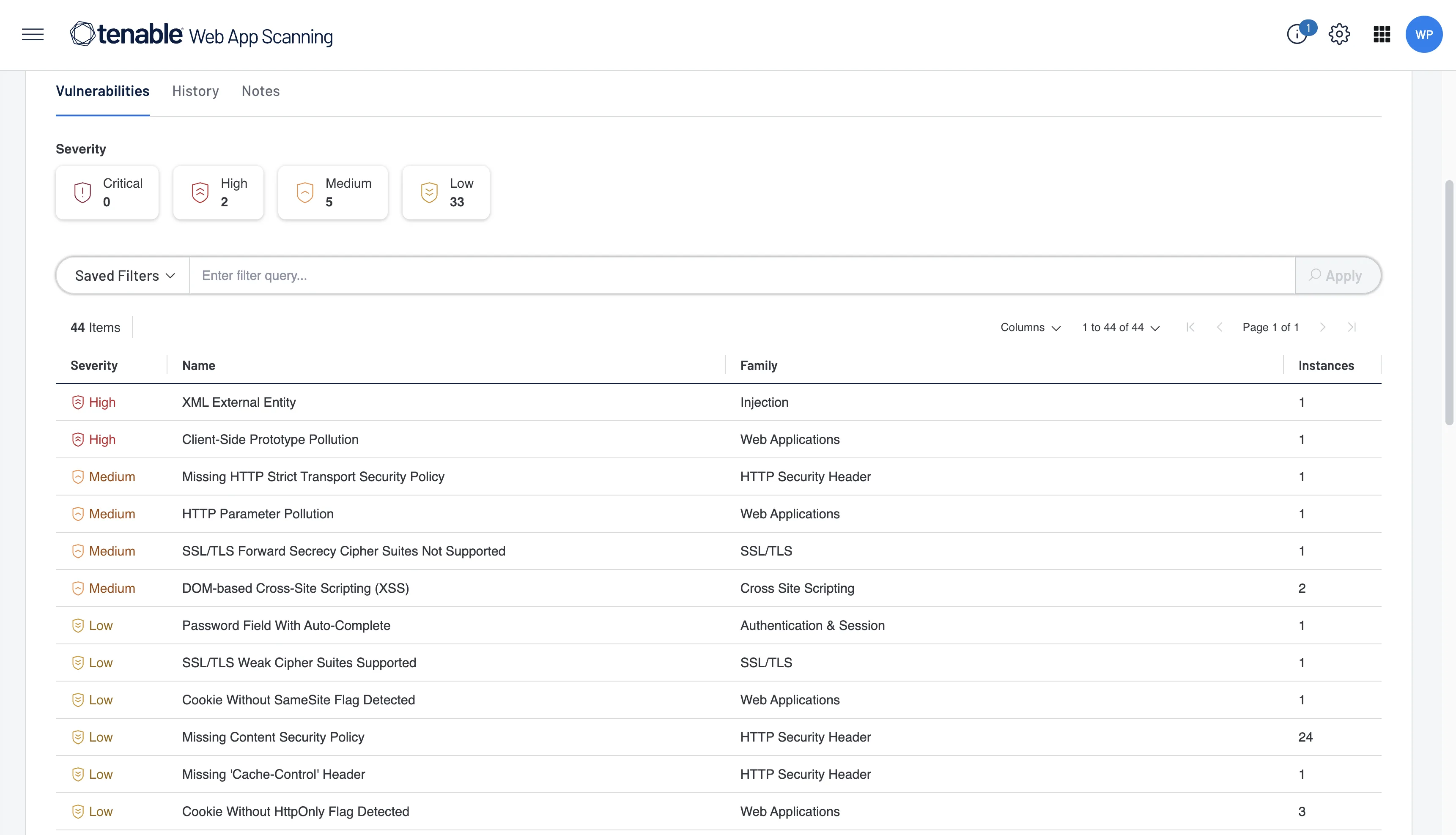
Scan Controls
Tenable gives you granular control over scan behavior:
- Pause/Resume: Stop scans during maintenance windows and pick up where you left off
- Rate Limiting: Throttle request rates to avoid hammering production systems
- Scheduling: Recurring scans on custom schedules (weekly, monthly)
- Scope Control: Include and exclude URL patterns to focus scanning where it matters
Custom Dashboards
The platform lets you build custom dashboards and visualizations. You can combine web app vulnerability data with infrastructure findings from Tenable.io for a combined view of your attack surface.
Integrations
Getting Started
CLI and API Usage
# Set up API credentials
export TENABLE_ACCESS_KEY="your-access-key"
export TENABLE_SECRET_KEY="your-secret-key"
# Create a new web application scan
curl -X POST "https://cloud.tenable.com/was/v2/scans" \
-H "X-ApiKeys: accessKey=$TENABLE_ACCESS_KEY;secretKey=$TENABLE_SECRET_KEY" \
-H "Content-Type: application/json" \
-d '{
"name": "Production App Scan",
"targets": ["https://app.example.com"],
"schedule": {
"enabled": true,
"type": "weekly"
}
}'
# Launch a scan
curl -X POST "https://cloud.tenable.com/was/v2/scans/{scan_id}/launch" \
-H "X-ApiKeys: accessKey=$TENABLE_ACCESS_KEY;secretKey=$TENABLE_SECRET_KEY"
A Python SDK is also available via pip install pytenable.
When to Use Tenable WAS
Tenable WAS makes sense for organizations already in the Tenable ecosystem. If you’re running Tenable.io for infrastructure vulnerability management, adding WAS gives you web app coverage in the same dashboard with correlated risk views.
Good fit for:
- Existing Tenable customers wanting unified web app and infrastructure security data
- Teams needing API testing across REST, GraphQL, and SOAP services
- Organizations that want ASM integration for automatic discovery of unknown web apps
- Government or regulated environments needing FedRAMP-authorized on-premises scanning
Not the best fit if:
- You need a free scanner — ZAP or Wapiti are open-source alternatives
- You’re scanning many small apps on a tight budget — per-FQDN pricing at $3,578/year adds up
- You need an air-gapped solution with no cloud dependency (Security Center helps, but WAS is cloud-first)
Comments
Powered by Giscus — comments are stored in GitHub Discussions.